Some of the data Iran used to unleash a deluge of emails designed to intimidate U.S. voters just weeks before the country’s presidential election came directly from one state’s voter registration database.
U.S. officials confirmed the finding late Friday in an alert issued by the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA), which has been coordinating U.S. election security efforts.
The alert said Iranian hackers targeting websites belonging to various U.S. states, including state election websites, “successfully obtained voter registration data in at least one state” by exploiting what it described as website misconfigurations.
That data was then used as part of an Iranian campaign last week to intimidate voters in at least four states, including Arizona, Alaska, Pennsylvania and Florida.
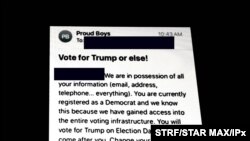
The “spoofed” emails were designed to make it look as though they had come from the Proud Boys, a far-right group that has rallied behind President Donald Trump.
The text of the emails warned voters, “You will vote for Trump on Election Day or we will come after you.”
According to the latest alert, the hacked voter registration information was also featured in a video disseminated by Iran implying that some voters might be prone to casting fraudulent ballots.
Just 27 hours
Iran’s foreign ministry last week rejected the U.S. accusations as “baseless,” and summoned the Swiss ambassador, who represents U.S. interests in Iran because the two countries do not have diplomatic relations.
However, Cyberscoop, a publication that focuses on cybersecurity, cited U.S. officials Friday as saying the Iranian hackers targeted websites in 10 different states.
Despite Iran’s initial success in penetrating a key database, it took U.S. intelligence officials just 27 hours to trace the emails and the video back to Tehran, sharing the information with U.S. states ahead of a public announcement featuring Director of National Intelligence John Ratcliffe and FBI Director Christopher Wray.
Ratcliffe described the Iranian operation as a “desperate” attempt to sow chaos and confusion, adding that when it came to the video, “any claims about such allegedly fraudulent ballots are not true.”
U.S. security and intelligence officials Friday said they remain confident that the upcoming election, set for November 3, will be the most secure in modern history. Officials said that despite the data breach, voting infrastructure in all 50 states remains resilient, with up to 95% of states now having systems in place to ensure there is a paper record of every vote cast.
Still, they expressed concern that the U.S. could see a surge in attacks on election-related systems as the nation gets closer to Tuesday’s vote, noting Tehran has been aggressively flexing new capabilities.
"We wouldn't be surprised to see more website defacements," CISA Director Christopher Krebs told reporters earlier Friday, calling it, “a tried-and-true tactic of the Iranians."
He said Iran has also been known to use distributed denial of service attacks (DDoS), which block access to websites by overwhelming the server hosting the site with internet traffic.
'Iran's capabilities are growing'
Researchers, though, caution against overplaying Iran’s cyber capabilities just based on the intimidation emails and the video.
“It was a combination of the kinds of tools that spammers use to get out lots of messages, along with a pretty ham-fisted attempt at trying to get some of the narrative around this traction on social media,” John Scott-Railton, a senior researcher with The Citizen Lab at the University of Toronto's Munk School, told VOA after the initial salvo.
“What it felt like was a group that could do certain things well but didn't necessarily have a great idea about how to do some of the more nuanced, sort of culturally sensitive things that go into doing a disinformation campaign,” he said.
But Scott-Railton also said that could change.
“Iran's capabilities are growing and they're learning. And each tango with this kind of thing results in an evolution and maybe an improvement for the next time around,” he said.
In the meantime, U.S. officials are bracing for more, whether from Iran or from Russia, which also has managed to access voter registration databases, though intelligence and election officials now describe what the Russians got as products based on the data, and not the data itself.
Other U.S. adversaries might also try to build on what they perceive as a sense of vulnerability.
“I would expect claims from any number of actors that maybe they’ve been able to manipulate [data or websites],” Krebs said, though he warned in many cases the claims will far exceed their actual capabilities.