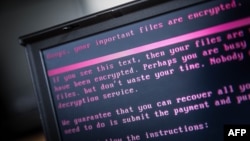
Several companies around the world continue to report outages and damage from Tuesday's massive Petya cyberattack that hit firms in more than 60 countries.
Heritage Valley Health System, a network of medical offices in the U.S. state of Pennsylvania reported Thursday it still could not provide lab or diagnostic testing to patients. The company said some surgeries had to be canceled and and its satellite offices had been closed since Wednesday.
The large Danish shipping company A.P. Moller-Maersk – one of the largest companies hit by the cyberattack – said it had restored operations at some of its terminals, but others remained inoperable.
A.P. Moller-Maersk said it couldn’t be specific about how many sites were affected, but noted some terminals are “operating slower than usual or with limited functionality.”
Similarities to WannaCry
Europol director Rob Wainwright called Tuesday’s hack “another serious ransomware attack.” He said it bore resemblances to the previous ‘WannaCry’ hack, but it also showed indications of a "more sophisticated attack capability intended to exploit a range of vulnerabilities."
The WannaCry hack sent a wave of crippling ransomware to hospitals across Britain in May, causing the hospitals to divert ambulances and cancel surgeries. The program demanded a ransom to unlock access to files stored on infected machines.
Researchers eventually found a way to thwart the hack, but only after about 300 people had already paid the ransom.
The most recent hack has been largely contained, but now some researchers are questioning the motivation behind the attack. They say it may not have been designed to collect a ransom, but instead to simply destroy data.
“There may be a more nefarious motive behind the attack,” Gavin O'Gorman, an investigator with U.S. antivirus firm Symantec, said in a blog post. “Perhaps this attack was never intended to make money [but] rather to simply disrupt a large number of Ukrainian organizations.”
Russian anti-virus firm Kaspersky Lab similarly noted that the code used in the hacking software wouldn’t have allowed its authors to decrypt the stolen data after a ransom had been paid.
"It appears it was designed as a wiper pretending to be ransomware," Kapersky researchers Anton Ivanov and Orkhan Mamedov wrote in a blog post. “This is the worst-case news for the victims – even if they pay the ransom they will not get their data back.”
NSA tools
The computer virus used in the attack includes code known as Eternal Blue, a tool developed by the NSA that exploited Microsoft's Windows operating system, and which was published on the internet in April by a group called Shadowbrokers. Microsoft released a patch in March to protect systems from that vulnerability.
Tim Rawlins, director of the Britain-based cybersecurity consultancy NCC Group, said these attacks continue to happen because people have not been keeping up with effectively patching their computers.
"This is a repeat WannaCry type of outbreak and it really comes down to the fact that people are not focusing on what they should be focusing on, the very simple premise of patching your systems," Rawlins told VOA.