In the first case of its kind, the U.S. Justice Department announced charges Wednesday against two Iranian hackers for allegedly launching so-called ransomware on the computer networks of U.S. municipalities, hospitals and other public institutions and extorting millions of dollars.
Ransomware is a type of malware used by cybercriminals to lock down computers and extort money from their users in exchange for providing the keys to unlock them. Once used primarily against individuals, ransomware has been increasingly employed in cyberattacks on businesses.
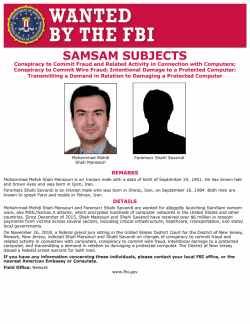
Faramarz Shahi Savandi, 34, and Mohammad Mehdi Shah Mansouri, 27, are accused of creating the SamSam Ransomware in December 2015 and installing it on the computer networks of more than 230 public and private entities in the United States and Canada, according to a 26-page indictment unsealed Wednesday.
With the targeted computer users unable to access their data, Savandi and Mansouri, operating out of Iran, would then demand a ransom payment made in the form of the virtual currency bitcoin in exchange for decryption keys for the encrypted data.
According to the indictment, the two Iranians received more than $6 million in cryptocurrencies from their victims which they converted into Iranian currency, or rial, using Iran-based bitcoin exchanges. About half of the infiltrated entities refused to make a ransom payment and suffered over $30 million in lost data, according to the indictment.
The victims included the cities of Atlanta, Newark and San Diego, the Colorado Department of Transportation, the University of Calgary in Calgary, Canada, and six U.S. public health care-related entities.
Deputy Attorney General Rod Rosenstein announced the six-count indictment at a press conference in Washington.
"Every sector of our economy is a target of malicious cyberactivity," Rosenstein said. "But the events described in this indictment highlight the urgent need for municipalities, public utilities, health care institutions, universities, and other public organizations to enhance their cybersecurity."
The two indicted Iranians remain at large and have been placed on the FBI's wanted list. They're charged with one count of conspiracy to commit wire fraud and two counts of intentional damage to a protected computer, among other related crimes.
The indictment marks the first time the Justice Department has brought charges against cybercriminals involved in a ransomware and extortion scheme, according to Rosenstein.
Ransomware has grown in sophistication and distribution in recent years. According to a report by the cybersecurity firm Bitdefender, ransomware payments were expected to reach a record $2 billion in 2017.
'Trend' from Iran
The charges are also the latest in a string of indictments brought against Iranian hackers and cybercriminals in recent months. In March, prosecutors charged nine Iranian hackers with penetrating the computer networks of hundreds of American and foreign universities and other institutions to steal valuable research material. Unlike some of the previously indicted Iranian hackers, however, Savandi and Mansouri are not believed to have ties to Tehran.
"The actions highlighted today, which represent a continuing trend of cybercriminal activity emanating from Iran, were particularly threatening, as they targeted public safety institutions, including U.S. hospital systems and governmental entities," said Amy Hess, executive assistant director of the FBI. "As cyberthreats evolve and cybercriminals develop more sophisticated techniques, so do we."
The 35-month computer hacking scheme led by Savandi and Mansouri began in January 2016 with an attack on an unidentified business in Mercer County, New Jersey, and moved on to public entities such as the City of Newark and health care providers such as Kansas Heart Hospital in Wichita, Kansas.
Assistant Attorney General Brian A. Benczkowski said the Iranian hackers carefully chose their targets. A few days prior to attacking the network of Kansas Heart Hospital, for example, they "conducted online searches concerning the hospital and accessed its website," he said.
Kimberly Goody, manager of cybercrime analysis at cybersecurity firm FireEye, said the hackers probably chose to target health care and government organizations because "they provide critical services and believed their likelihood of paying was higher as a result."
The indictment does not name the entities that paid a ransom.
Jeff Seldin contributed to this report.